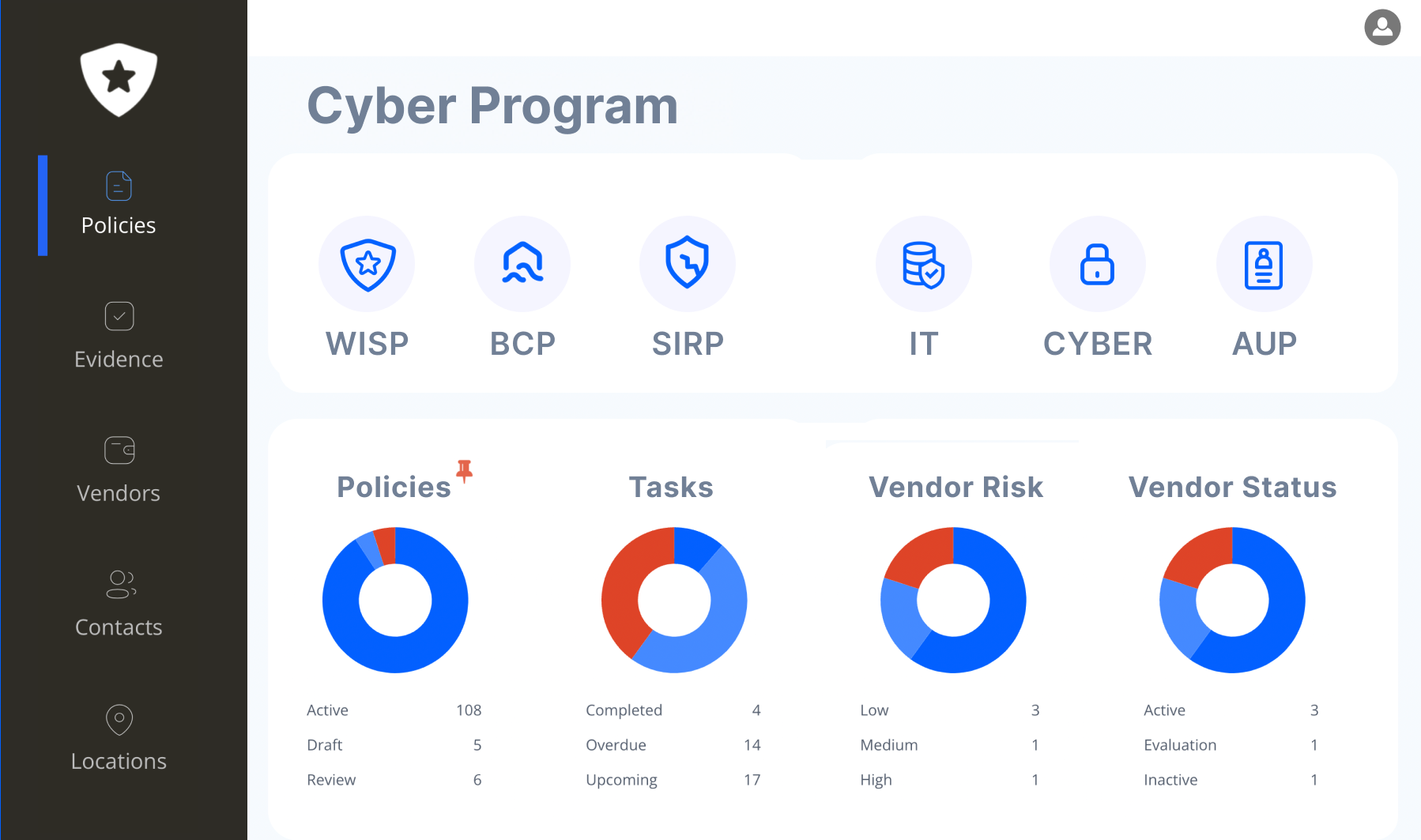
Cyber Program Management Platform
Risk Management
Information Security Policy
Business Continuity Plan
Security Incident Response Plan
Vendor Risk Management
Finally meet cyber regulations
LATEST NEWS / NOV 9, 2023
Buckler Announces New Strategic Relationship with LPL Financial by Joining the Vendor Affinity Program

"Adding Buckler to our Vendor Affinity Program will help simplify the process for advisors"
Alex Russell, LPL CISO
30-Question Compliance Self-Assessment
APRIL 15th DEADLINE
Access All The Required Documentation For The NYDFS 23 NYCRR 500 2nd Amendment In A Single Location

Buckler
Overview
in 2 minutes
















BUCKLER WON THE
2023 T3 Emerging Technology Award
"Everyone should have Buckler"
Joel Bruckenstein, T3 Technology Tools for Today CEO
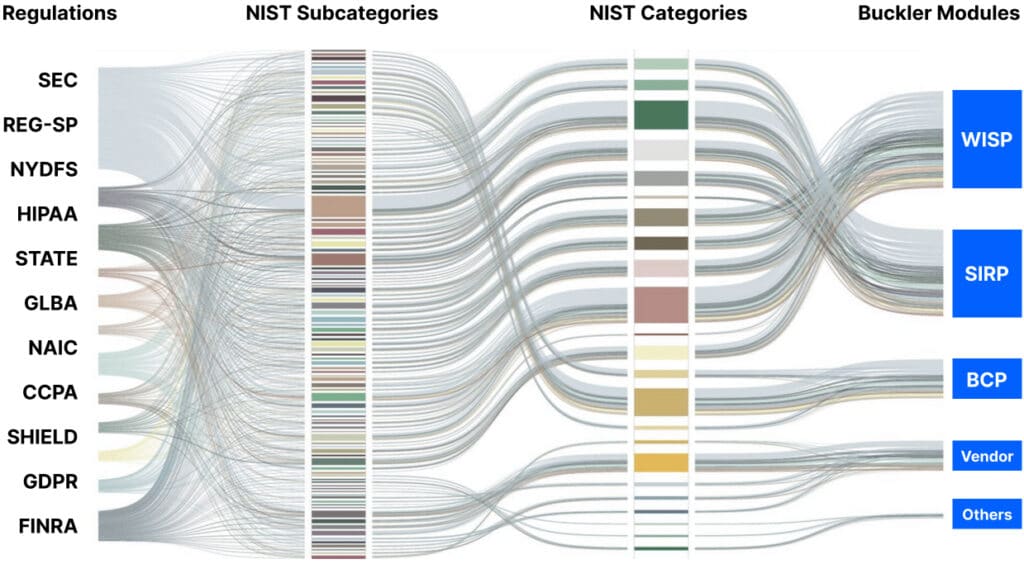
Regulatory & Audit Expectations
Challenges Buckler Addresses
Multiple
Regulations
There are multiple laws, guidelines, risk alerts, and recommendations to follow.
Meeting
Deadlines
For compliance, periodic tasks are monthly, quarterly or yearly.
Assigning Responsibilities
Tasks fall across a range of people and teams to ensure accountability.
Reaching Full Compliance
It’s a mountain, not a hill to ensure full compliance and stay audit-ready.
Meet Financial Services Cyber Regulations
With One Single Innovative & Integrated System












Buckler’s Secret Sauce
One Buckler Policy Matches Multiple Policies from Multiple Regulations
Become Audit-Ready With
Buckler Modules
Written Information Security Policy
Built-in data and technical controls, safeguards and cybersecurity minimum standards
Security Incident Response Plan
Policies and procedures to know exactly what to do when you have a security incident or a breach
Business Continuity & Disaster Recovery Plan
Plan for what to do when you have a significant business disruption event (pandemic, flood, hurricane, etc.)
Vendor Risk Management
Due diligence of all vendors accessing, storing, or controlling private data
Compliance-Driven
Experience the Difference
Buckler was created by security experts who understand regulatory compliance requirements and the challenges firms have to keep up with their evolution.
Policy Efficiency
Clients rave about the organization Buckler provides to meet multiple regulatory standards within one environment. The heavy lifting of sorting policies is done.
Adapt & Adopt Policies
Reminders & Alerts
Using a calendar, administrators can assign tasks and roles within Buckler based on policy frequency of action to ensure full compliance over time.
Never Miss a Deadline
Get Listed as a vCISO in the Open VRM Vendor Directory
Promote your compliance, increase findability and Client opportunities
- Register as a Vendor in Open VRM
- Fill a Questionnaire and upload your Cyber Package
- Get listed in the Open VRM Vendor Directory as a vCISO expert
Become a Buckler & Open VRM vCISO Network Partner
Offer CPMS (Cyber Program Management Services) to your Clients using Buckler
- Register as a vCISO Network Partner
- Have your own Risk Assessment Questionnaire added in Buckler
- Offer Cyber Program Management Services (CPMS) to Buckler Clients
Are you a Vendor?
Read about Open VRM, Buckler's Freemium model to help you Better Serve Your Clients
The Open Vendor Risk Management Standard for Financial Services
Open VRM
A Vendor Risk Management (VRM) Platform for Vendors and their Clients to Solve Multiple VRM Challenges in Harmony

Jeff Reed
CISO
“Buckler allows me to save precious hours every week.”

Frequently Asked Questions
Book a call to get a demo. If you like what you see, we will send you a link to our payment portal: You accept the terms, enter your credit card, and voilà! In a maximum of 2 business days, you will receive your credentials.
A “Cyber Progam” is what regulators call the complete set of documents and plans you must have to be compliant: Written Information Security Policy (WISP), Business Continuity Plan (BCP), Security Incident Response Plan (SIRP), and Vendor Management. The challenge to stay compliant gets deeper as documents with only policies are not enough for proof of compliance. We created a multi-regulatory management system that allows you to track policies, assign them, get alerts and further document the tasks as evidence in one location.
Depending on the experience of your Chief Information Security Officer (CISO), or someone assigned to cybersecurity, it varies between a few hours to a few days.
Buckler (nor any other policy management system) can’t create compliance. To be compliant, it is up to you to do the actions listed in the policies! To ease the compliance burden, Buckler provides all the policies required to meet the cybersecurity regulations you select into one simple, comprehensive cyber program.
Yes of course! Buckler comes with the full list of policies from major cyber regulations (with ongoing updates) but you can add your own.
Always know that Buckler does not access, store, or control any of your client’s private data. The only thing we have is information about your cyber program but yes, we eat our own dog food! We use Buckler and protect your cyber program data as defined in our own privacy policy.
We do not do audits. However, in Buckler, we provide a questionnaire for self-audits. We can also refer you to consulting firms who perform Security Risk Assessments.
Buckler is a Software-as-a-Service (SaaS) system. There is nothing to install or update.
Yes, just let us know and we will quickly set it up for you.
More regulators are moving towards the NYDFS model of requiring a comprehensive cybersecurity program.
Extras!
For your Employees & Affiliates

Cyber Awareness Training
A proven educational framework that drives behavior change and real security outcomes.

Phishing Campaigns
A poweful phishing email system to test users and provide automated remedial training.

Acceptable Use Policy (AUP)
A customizable document outlining a set of rules to be signed by your employees.